Highlight

Successful together – our valantic Team.
Meet the people who bring passion and accountability to driving success at valantic.
Get to know usFrom the first alarm to restart
Cyber crises happen. The decisive factor is what happens next. Our Incident Response Service enables you to act immediately. With an experienced team, reliable partners and seamless preparation.


Disaster Cyber Attack: What to do when a disaster strikes...
What to do when nothing works anymore? This white paper uses a real-life cyber incident to show you how to steer your company through the crisis and which decisions will…
More than 330.000 attacks per year
Exceptional situations require exceptional partners
The threat of cybercrime remains high in Germany. According to police crime statistics (Polizeiliche Kriminalstatistik, PKS), 131,391 cases of cybercrime were registered in 2024. In addition, there were a further 201,877 cases in which the perpetrators operated from abroad or from an unknown location (BKA, 2024). These and many other surveys make it clear that companies are exposed to a constant digital threat, regardless of industry and size.
Companies that fail to prepare comprehensively risk not only financial damage, but also significant reputational damage and regulatory sanctions. While companies often recognize the urgency of taking action and even have contingency plans in place in case of doubt, there is usually a lack of practical experience. There is a lack of clear roles, coordinated procedures and a validated recovery strategy. These deficits become apparent in an emergency at the latest, when delays, information gaps and wrong decisions occur despite the emergency plan, which increase the damage.
When a cyber attack occurs, there is often chaos: systems fail, data is encrypted, internal and external bodies demand information, decisions have to be made under high pressure. This raises questions such as:
We have experienced in numerous cases what it means when nothing works anymore. Together with board members and managing directors, we have supported organizations in exceptional circumstances to maintain supply chains, ensure the operation of retail stores, keep production lines running and secure cash flows.

In collaboration with the responsible parties and experts from our network, we were able to make the disaster manageable while taking into account the requirements of the stakeholders – whether owners, suppliers, customers or authorities. Our success is not only reflected in the rapid restoration of business activities and the satisfaction of our customers, but is also confirmed by independent auditors.
Whether ransomware, targeted attack or technical failure...
...the decisive moment is about more than IT
Preparing for a cyber incident is often seen as an IT issue, but in terms of business continuity management, it is an issue for the entire company. In the event of an attack, relying solely on technology means that important business processes are down for longer than necessary and that priorities, alternative solutions and emergency measures have to be laboriously worked out during the crisis. This costs time and money – in two respects.
In an emergency, the interaction between different parties is crucial to the success of damage limitation. As a central component of corporate resilience, a sophisticated incident response approach must be multidisciplinary and bring together cyber security, management, legal, communication and external partners such as forensic experts and authorities.
A holistic incident response approach…

The increase in successful attacks – mostly ransomware attacks¹ – that partially or completely paralyze companies has changed the focus on IT. It has suddenly become clear that nothing works without IT. Accordingly, the time after a cyber incident is discovered is particularly critical. This is when it is crucial to quickly contain the attack and restore business processes to pre-crisis levels with as little downtime as possible. This includes immediate measures, stakeholder-oriented communication, compliance with legal requirements and the restoration of business processes prioritized according to their importance for the company. In order to organize this restart effectively, many years of experience are required not only in the operation of IT infrastructures, but above all in the entrepreneurial evaluation of the procedure in such crises.
Our goal: maximum security with minimum impact on your business operations
On request, our experienced crisis team will take over the operational management of the crisis team and will be at your side around the clock. Our aim is to ensure maximum security while minimizing the impact on your ongoing business activities.
External crisis expertise
Your advantages at a glance
In a crisis, speed, clarity and experience count. As external crisis experts, we provide immediate relief, establish structures and bring decision-making certainty to uncertain situations. Your added value at a glance:
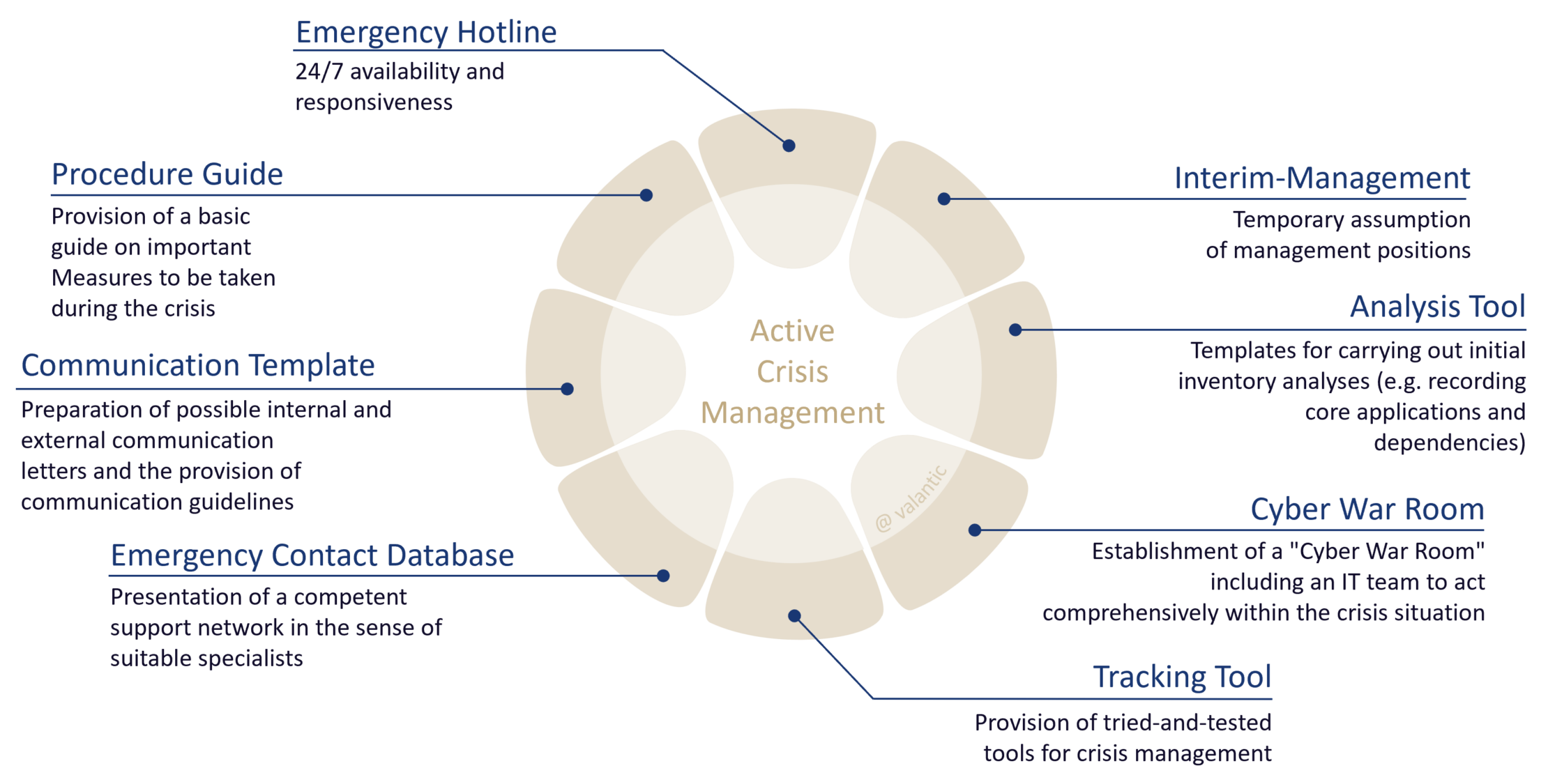
The best defense is preparation
Not every incident leads to a crisis – but every cyber crisis starts with an incident. The right preparation is crucial for the outcome.
Many companies have a crisis plan, but no established practice. In the event of an emergency, there is often a lack of clearly defined roles, coordinated decision-making channels and reliable interaction between IT, management and specialist departments. The result: delays, uncertainty, reputational damage and economic losses.
Crisis readiness means making the organization capable of acting – under stress, with limited information and against the clock. This is not just about technical responses, but above all about communication, prioritization and the interaction of all stakeholders. If you want to react confidently in a crisis, you need to train regularly beforehand.
Resilient crisis management is based on the following elements:
Our experience shows: preparation is not a one-off project, but a continuous maturing process. Only those who run through real scenarios, clarify responsibilities and simulate decisions under pressure will not be surprised in an emergency.
Unsure whether you are prepared for the crisis?
Let’s rehearse the emergency.

References

Marc O'Polo stands for high-quality, contemporary premium modern casual clothing.
In our video success story, the customer reports on the consequences of the cyberattack and how, together with valantic, they rebuilt all compromised systems in a targeted manner and minimized the corresponding security risks in the long term and how they are setting up their IT landscape for the future.
During a highly critical cyber incident, we were able to work very focused on solving the problem thanks to valantic's fast, uncomplicated and expert help. [...] Above all, however, the collaboration was characterized by a high level of personal commitment, professionalism and pleasant cooperation.
Dr. Patric Spethmann, COO





Downloads
Your contact in case of emergency
The time immediately after a cyber incident is crucial. Those who are prepared can quickly contain the attack and get the most important business processes back up and running as quickly as possible. This requires a holistic view that combines IT, management and communication – and a well-coordinated team that can act confidently in an emergency.

Thomas Lang
Partner & Managing Director
valantic Division Digital Strategy & Analytics
¹In Germany alone, 950 ransomware attacks were reported in 2024 (number of unreported cases probably higher) (BKA, 2024).