SAP Add for authorization management
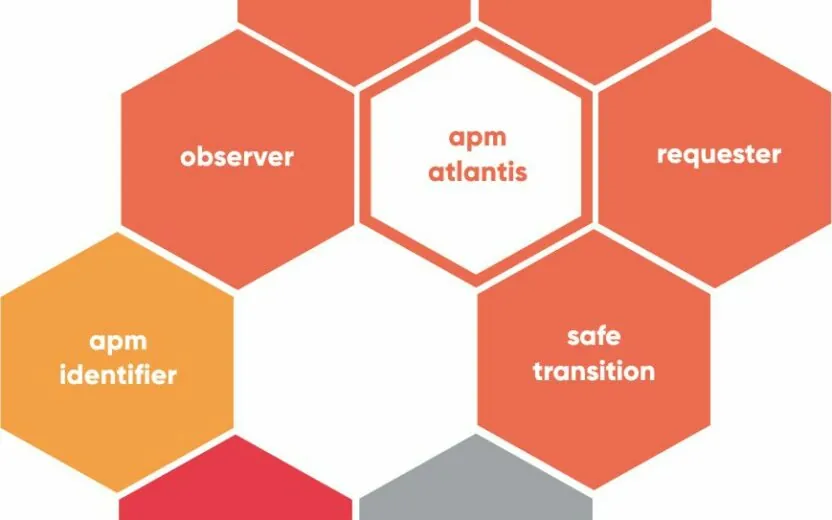
SAP Add on: apm atlantis
In addition to the basic module, the solution consists of the components apm composer (role creation), apm observer (evaluation and analysis), apm transformer (mass changes) and apm requester (role request system).